If you have deployed Azure Conditional Access (Azure MFA) you might have indirectly broken Microsoft Flow and impacted some service accounts used for running a business critical workflow. It is possible to make an exception with Azure Conditional Access that does not block your Microsoft Flow from working.
Example of issue: PowerUsers: MFA and Invalid Connection in Flow
You can use the workaround below to get Microsoft Flow to work as expected and still maintain some degree of security for your Microsoft Flow service account. I hope that Microsoft in the future will provide a better solution for running Microsoft flow for customers with Azure Conditional Access enabled. I’m not sure how they will handle this for simple end-users running Microsoft Flow and what happens on the back-end when the account tries to obtain a new Azure Access Token based on the Azure Primary Refresh Token or gaining access to the resources. I have added this to the list of things that the guys/girls in Redmond needs to explain one day.
Workaround
- Create an exception for the user in the existing “Azure Conditional Access” policy that is blocking the Microsoft Flow for doing it’s magic.
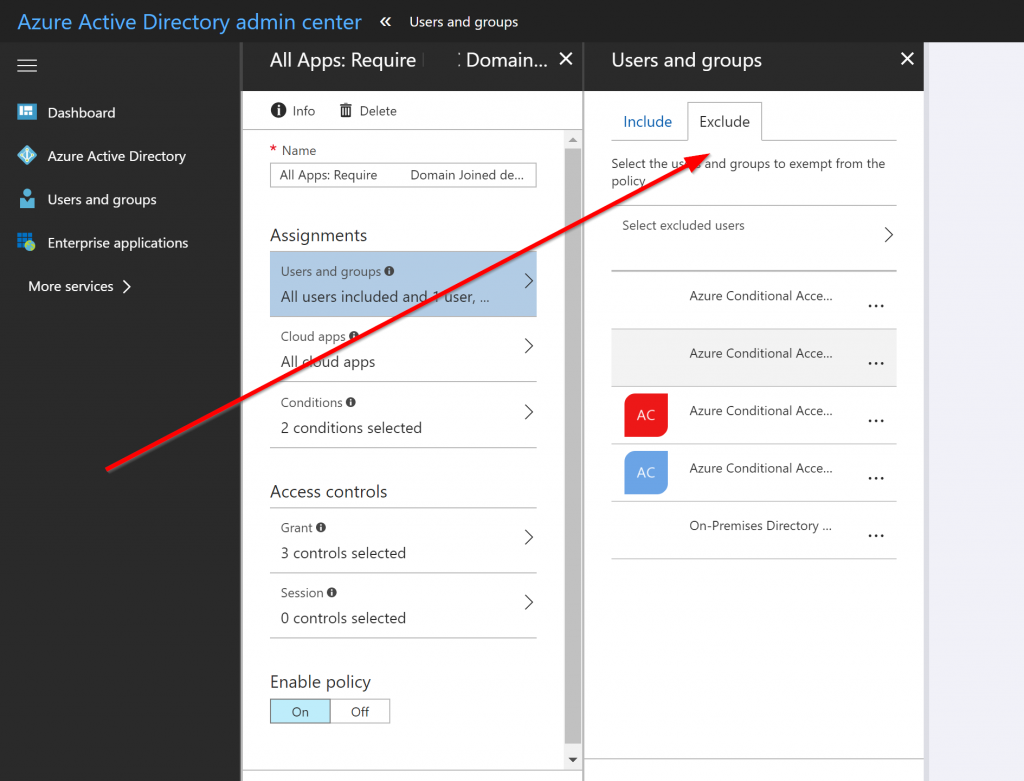
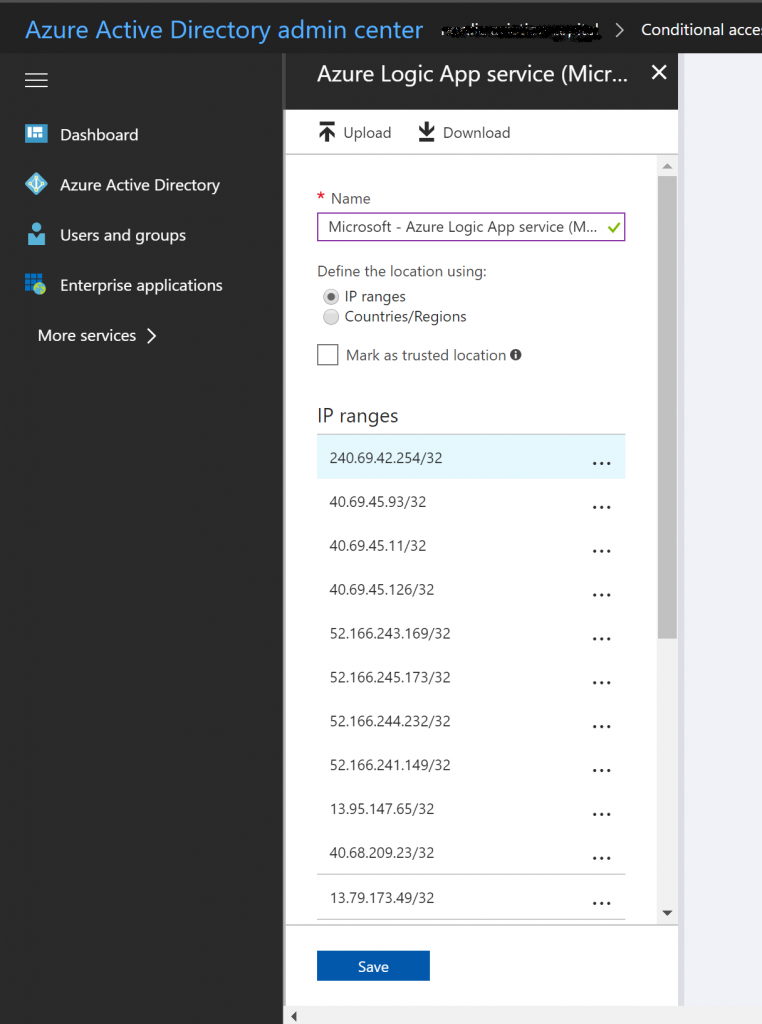
- Create a new “Network Location” under Azure Active Directory -> Conditional Access. Name the policy something like “Microsoft Azure Logic App – Microsoft Flow” and add the IP ranges for Microsoft Flow for your tenant region. Find the IP range associated with your tenant here: Limits and configuration in Microsoft Flow.
- Create a new “Azure Conditional Access” policy that “block acccess” for the specific Microsoft Flow user (or group of users) and the newly created “Network Location” as a “Exclusion” for this policy.
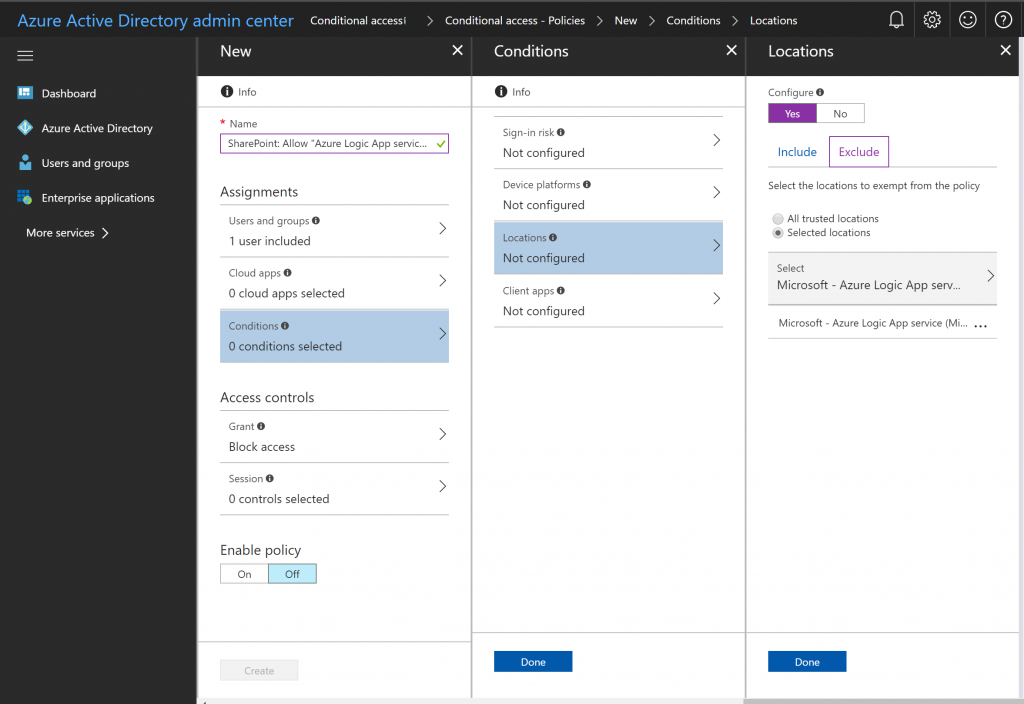
This should make your Microsoft Flow work again and retain some level of security for the accounts.
/Peter

Has Microsoft fixed this issue yet Peter?
Nice Post, I was looking to do this for users instead of Service accounts but maintain more security would the following work by excluding user from main MFA CA Policy and then create a new one that still uses MFA but excludes MS FLOW APP and add FLOW Location. The user would still be MFA for all o365 but excluded from MS flow – but I still feel that there some risk with that approach?
My under standing is
Block Approach: Allows MS Flow only
MFA + Excluded FLOW: Allows MS Flows + MFA enabled all O365.
Always handy to be aware of a workaround but I am surprised this issue wasn’t picked up during development
Hi Peter,
This is a good workaraound, but you need to comment about the license type you have and those where conditional access can be changed.
Regards
What about PowerApps connectors and mobile MFA?
Did the Microsoft Fixed this issue or not yet?
Thank you
[…] Microsoft Flow and Azure Conditional Access (Azure MFA) […]
Cloud apps should be microsoft sQL