Expired Active Directory users are still able to sign into Microsoft Office 365 / Azure Active Directory when using password Synchronization
If you have made the move from ADFS / PTA to using Azure AD Password Synchronization with SSO you will soon realize that former / terminated employees are still able to sign into Microsoft Office 365 / Azure Active Directory apps. This is due to the fact that Microsoft currently doesn’t have a mechanism for handling expired accounts in the Azure Active Directory.
Microsoft recommends using a PowerShell script that sets accounts as disabled once the user accounts expires in Active Directory. The reason is that Azure Active Directory Connects synchronizes the disabled state of user accounts from Active Directory with Azure Active Directory and prevents users from sign in (Block Sign In).
PowerShell Script
I wrote a PowerShell script that is available from the Microsoft Scripting Center and the Azure Automation runbook gallery. I recommend that you use Azure Automation for running this as a scheduled task daily.
Download the script from Microsoft Scripting Center or using the Azure runbook gallery.
Azure Automation Runbook
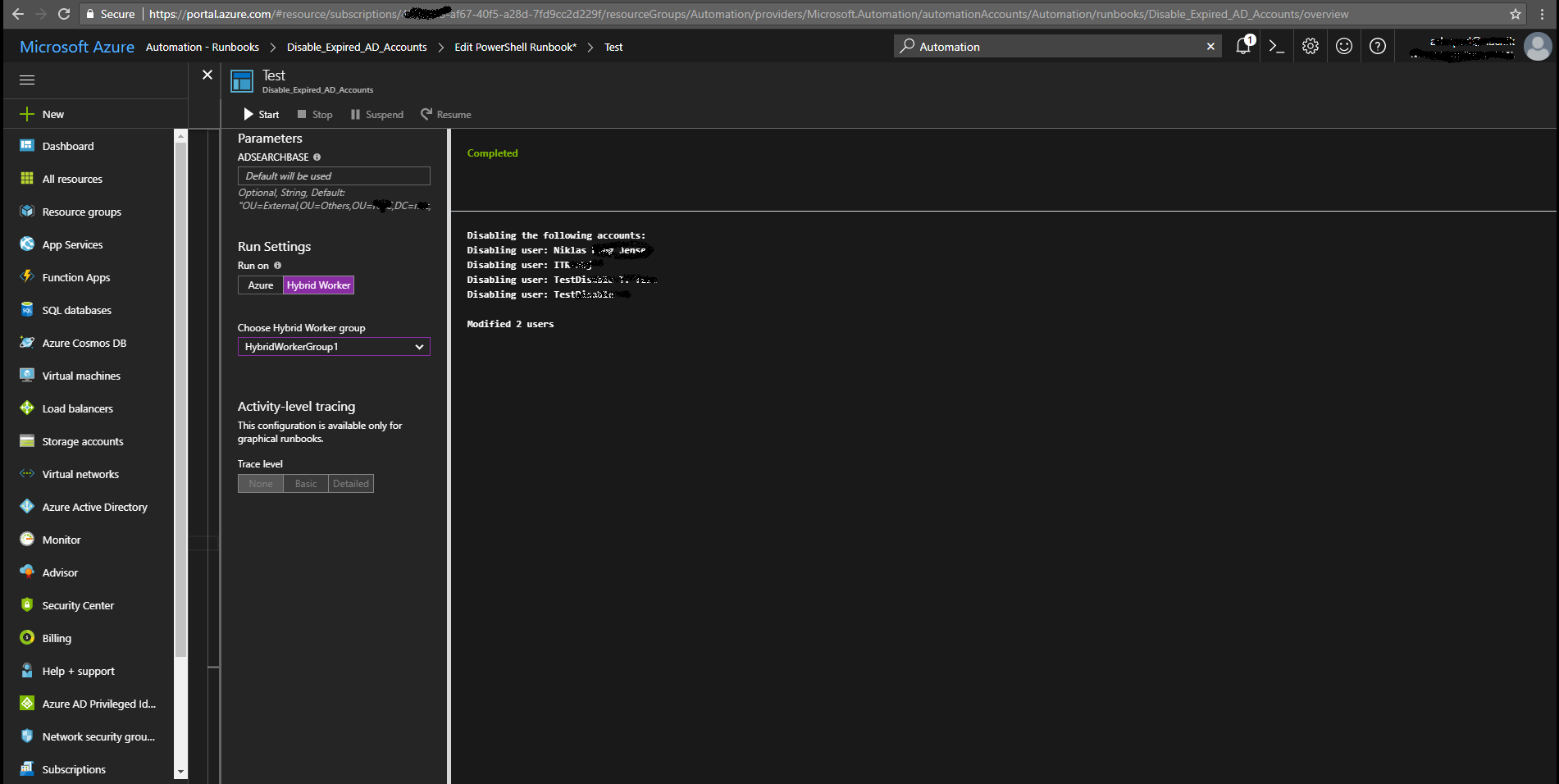
- Configure a OMS / Azure Automation Hybrid Worker on your domain controller or another server with an appropriate “run as account”
- The server needs to have the Active Directory PowerShell Module installed
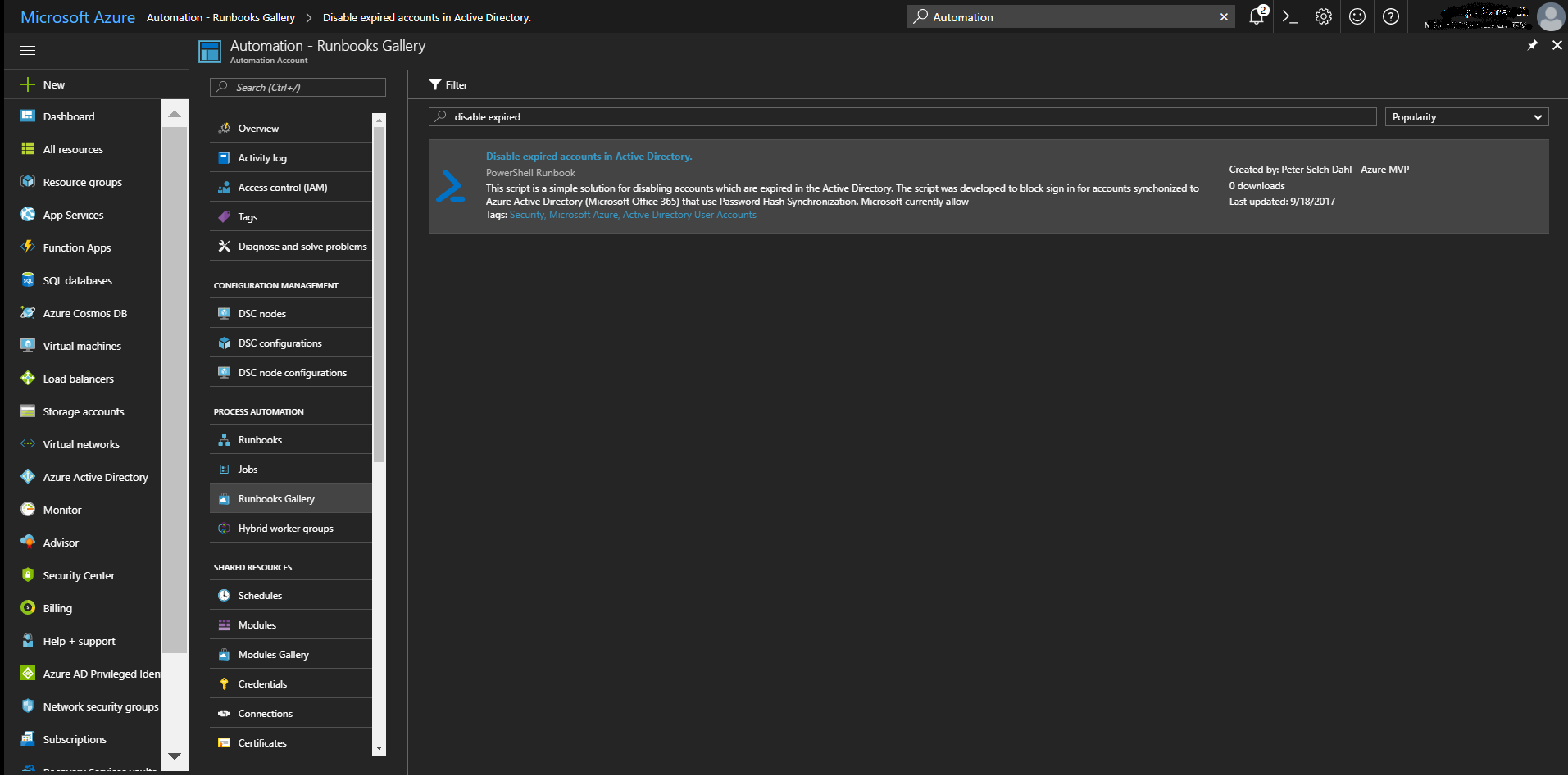
- Import the runbook “Disable expired accounts in Active Directory.” from the Azure runbook gallery. See here how: https://docs.microsoft.com/en-us/azure/automation/automation-runbook-gallery
Technical part
Azure Active Directory Connect will import disabled user accounts by checking that the “useraccountcontrol attribute” is set to 0x0002. The imported attribute will be mapped in the MetaVerse database to the “AccountEnabled” attribute in Azure Active Directory, which will be set to “false” to prevent / block sign in to Microsoft Office 365 or Azure Active Directory applications.
AAD Connect rule synchronization flow:
AD UserObjects (UserAccountControl) -> Azure AD Connect (MetaVerse DB) -> Azure AD Object (Account Enabled)
Azure AD Connect sync rules:
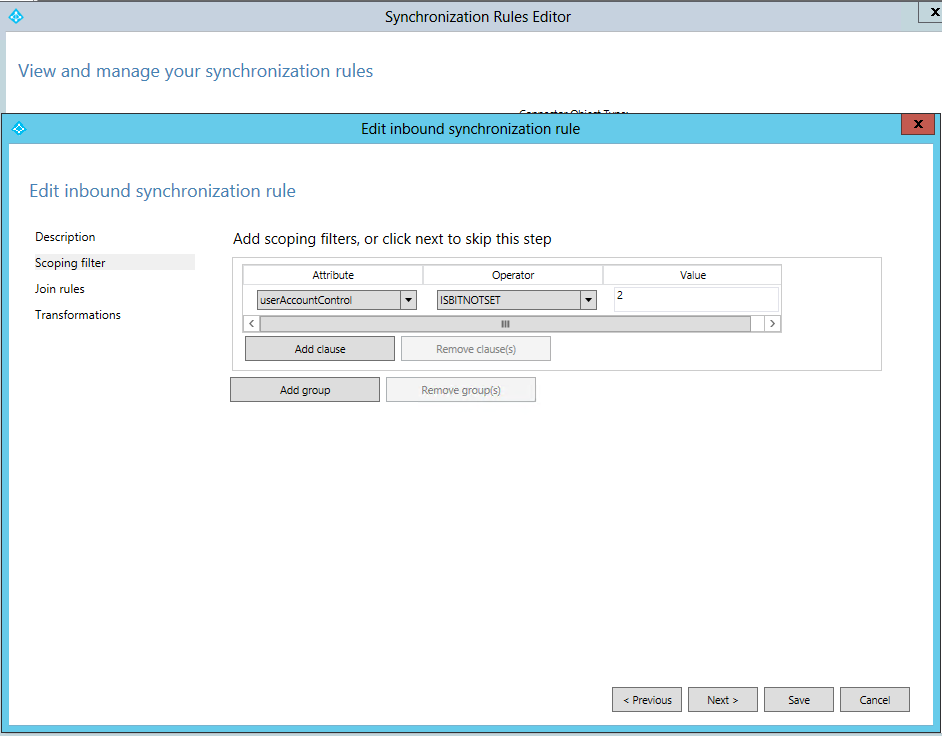
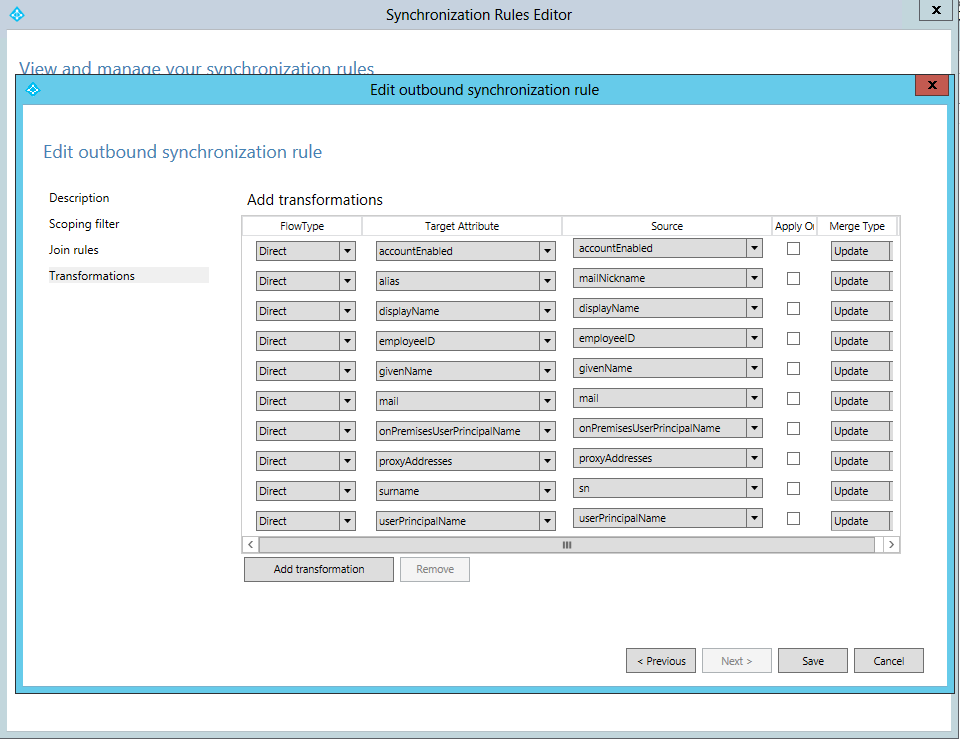
Azure Active Directory User attribute “AccountEnabled”:
The “AccountEnabled” attribute can be set both in the Microsoft Office 365 and the Azure Portal as the “Block Sign In” option. This is ONLY recommended for cloud-only users as the attribute will be overwritten during Azure AD Connect synchronization. Make sure you disable the users in the on-prem Active Directory.
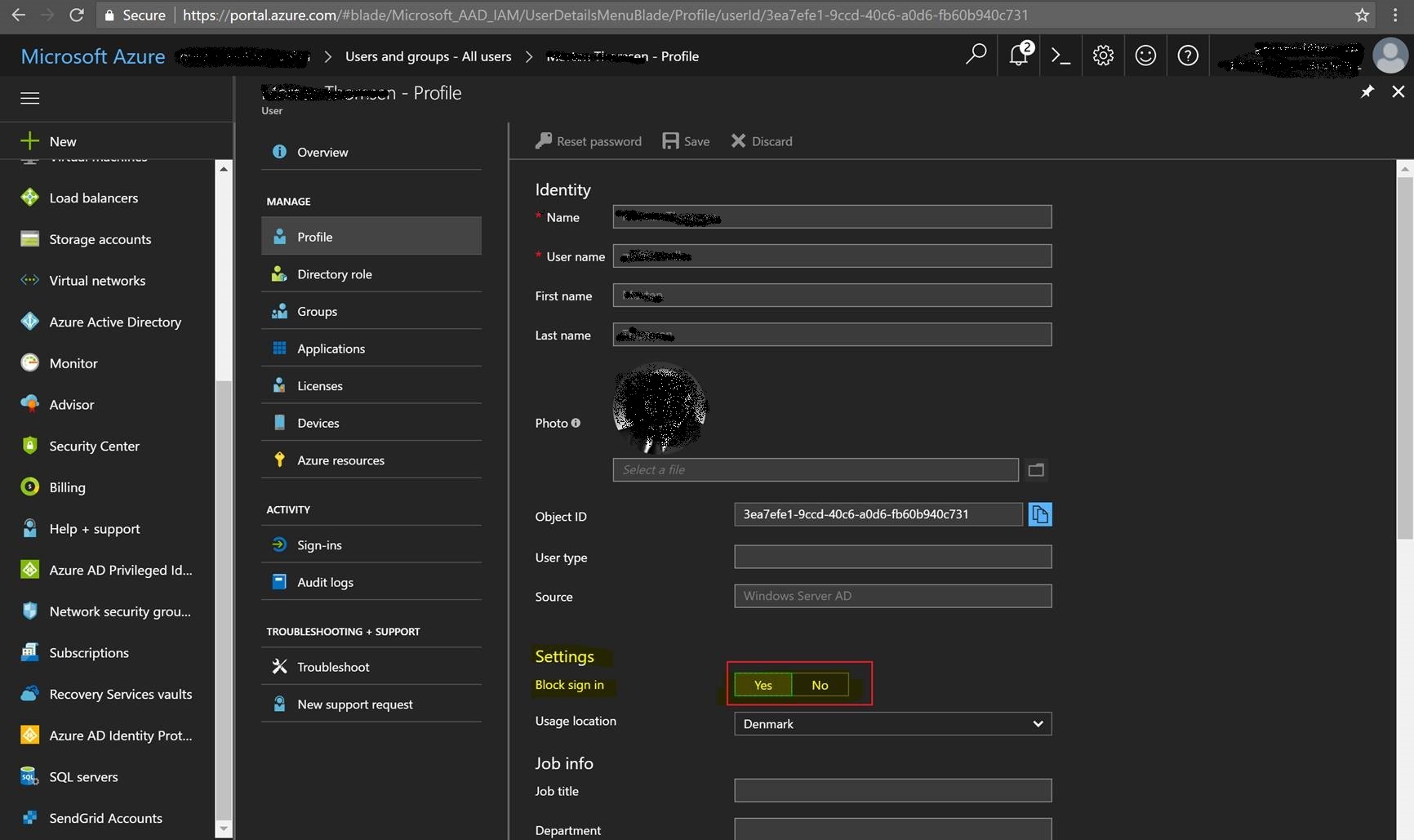
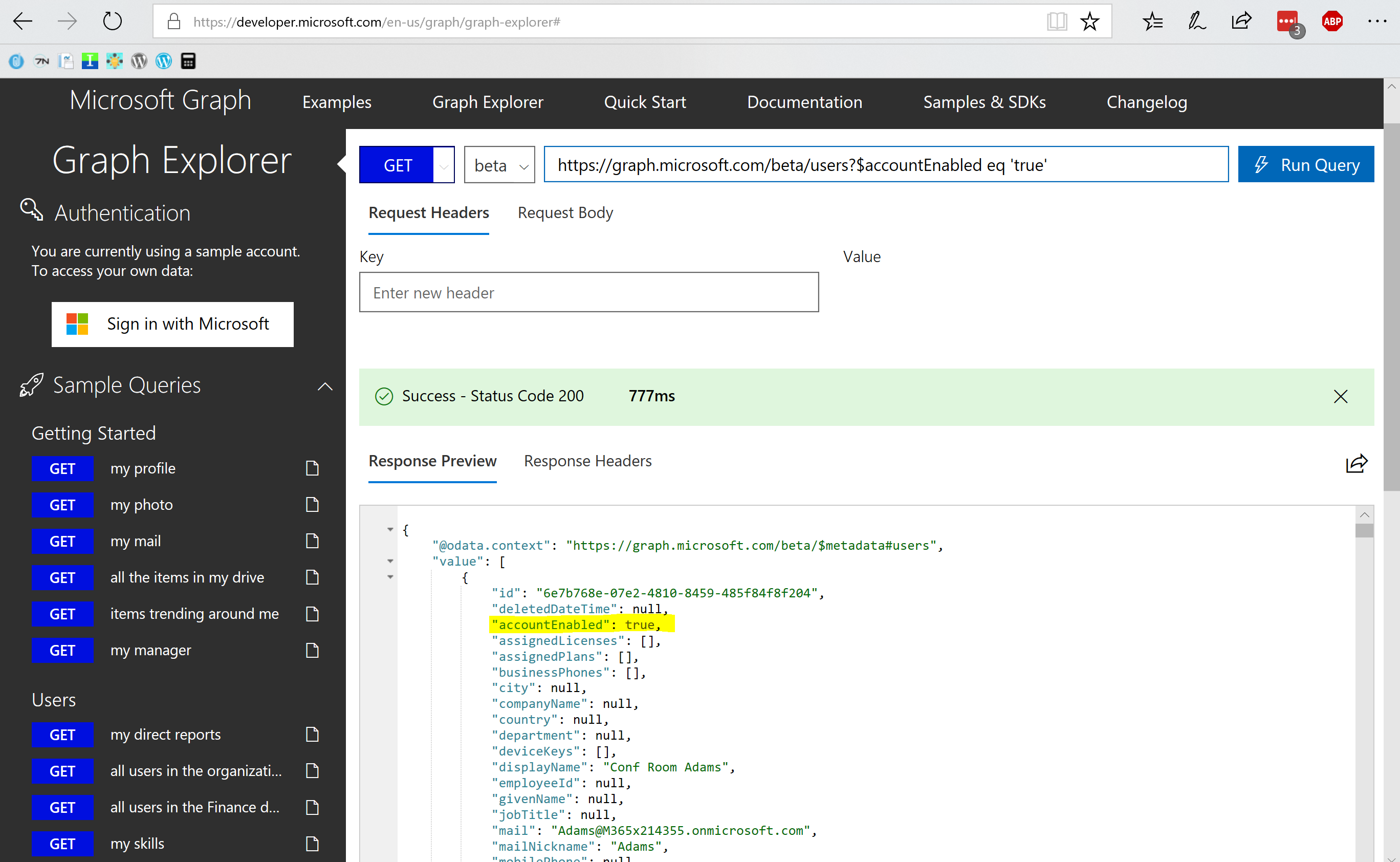
References:
- Use AAD Connect to disable accounts with expired on-premises passwords
- Implement password synchronization with Azure AD Connect sync
- Block Sign In Source-of-Authority issue
Tags:
AccountExpired, UserAccountControl
/Peter
Hi,
My good friend and I have been just discussing this subject, she actually is normally endeavouring to prove me incorrect! I will present her this particular blog post and rub it in a little!
http://alliancepro.co.in/2019/01/31/office-365-plans-in-india-office-365-for-business/
Very nice information here. Going to bookmark it!
Thank you for your refreshing article. It was a pleasure reading it. Look forward to more articles from you!
http://alliancepro.co.in/2019/01/31/office-365-plans-in-india-office-365-for-business/
Hello,
then if I would like to block some days o weeks a 365 account users (because they are not hire at this moment) but I need their AD account active, because I have forwarding email, or other services that login in AD.
What attribute I must modify?
[…] My colleague @peterselchdahl has got you covered if you need a detailed explanation, in his article “Block sign in for accounts with password hash sync”. […]
Hello,
The same question of Ramon Campos. Users in vacations, they must not access office 365, but their accounts must remain active to receive emails and remain on sharepoint teams.
What attribute I must modify?
Do you have another link for the script. I can’t seem to find it.