During the last couple of weeks I have been asked from a couple of my customers on how to get Azure device registration to work in environments using either Windows Credential Roaming or Roaming User Profile (with Certificates included).
After doing some research on the subject I found the answer on docs.microsoft.com, Microsoft doesn’t support using credential roaming / roaming user profile together with device registration for non-Windows 10 devices.
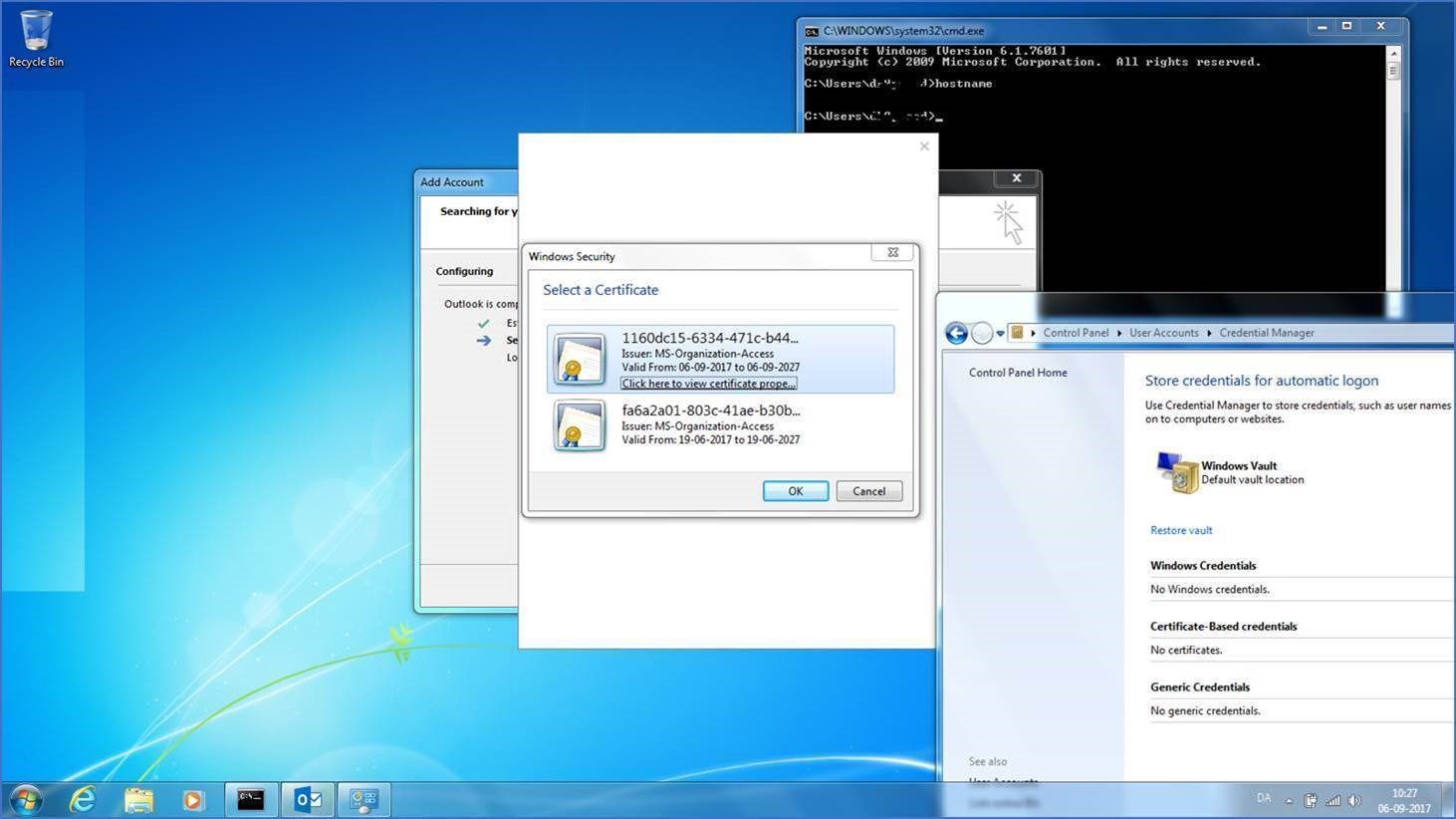
The biggest pain point is the fact that the users are getting asked to choose between multiple certificates enrolled previously on other servers/clients. As you see on the pictures below the end user is prompted in both Outlook and Internet Explorer. This does not provide a great end users experience especially if you are aiming for a single sign on experience.
I decided to analyse how the workplace agent for non-Windows 10 performed the enrollment. Using version 2.1 of the “Microsoft Workplace Join for non-Windows 10 computers” agent, the device registration occurs at log on and again 1 and 5 minutes after log on. It runs as a scheduled task in Windows.
Apparently the Workplace.exe keeps track of the certificate that it enrolled in the registry, which gave me the idea to write a PowerShell script for doing some house keeper and clean up all the old certificates. I have now tested the solution a couple of places and it seems to work very well. The script can be implemented as a scheduled task or using SCCM.
House keeping script for Credential Roaming
You can get the script from Microsoft Scripting Center.
Notes about the script:
- The script only perform clean up of certificates on clients running the “Workplace Join Client”.
- The script only deletes certificates issued from MS-Organization-Access.
- The script will only perform the clean up, if more then one MS-Organization-Access issued certificate exist in the store.
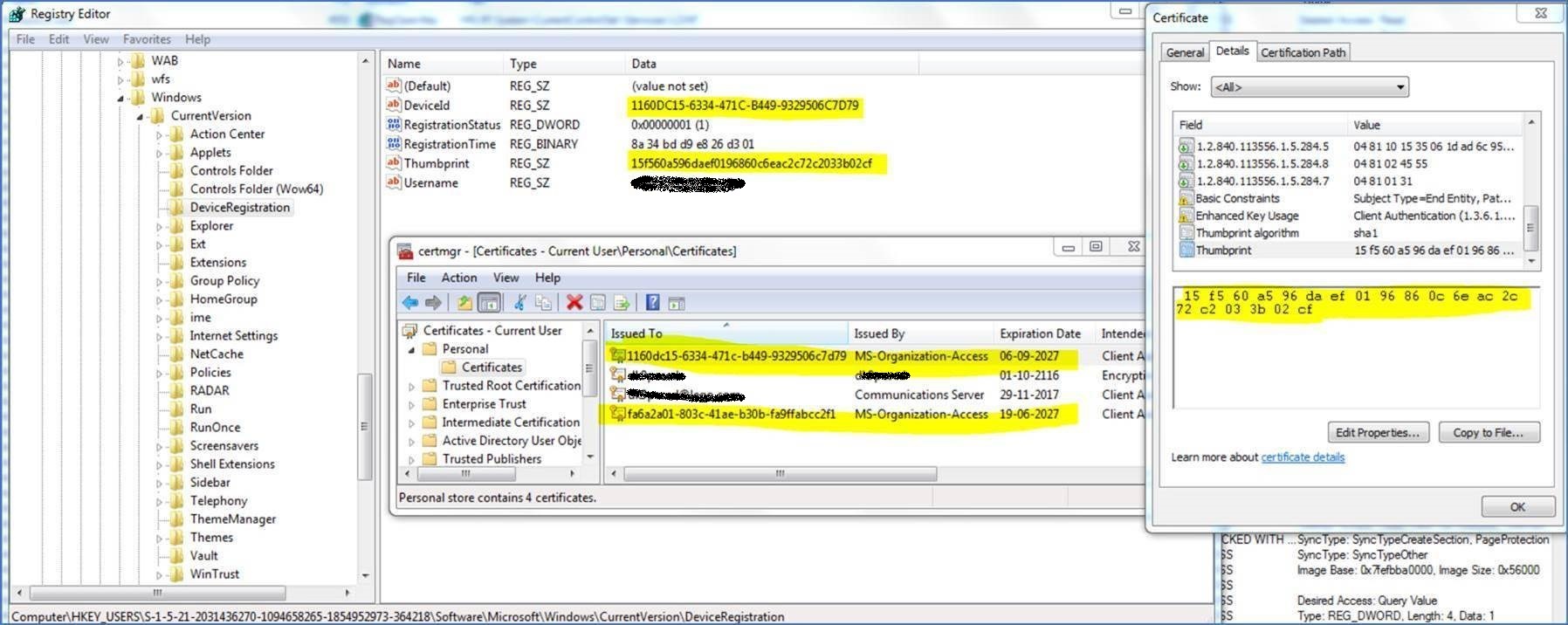
Finding the correct certificate for the specific computer
The “Microsoft Workplace Join for non-Windows 10 computers” agent stores the active certificate in the registry database (HKEY_Users\Software\Microsoft\Windows\CurrentVersion\DeviceRegistration) and keeps track of the re-enrolled from there.
Registration of down-level devices is NOT SUPPORTED for devices with roaming profiles
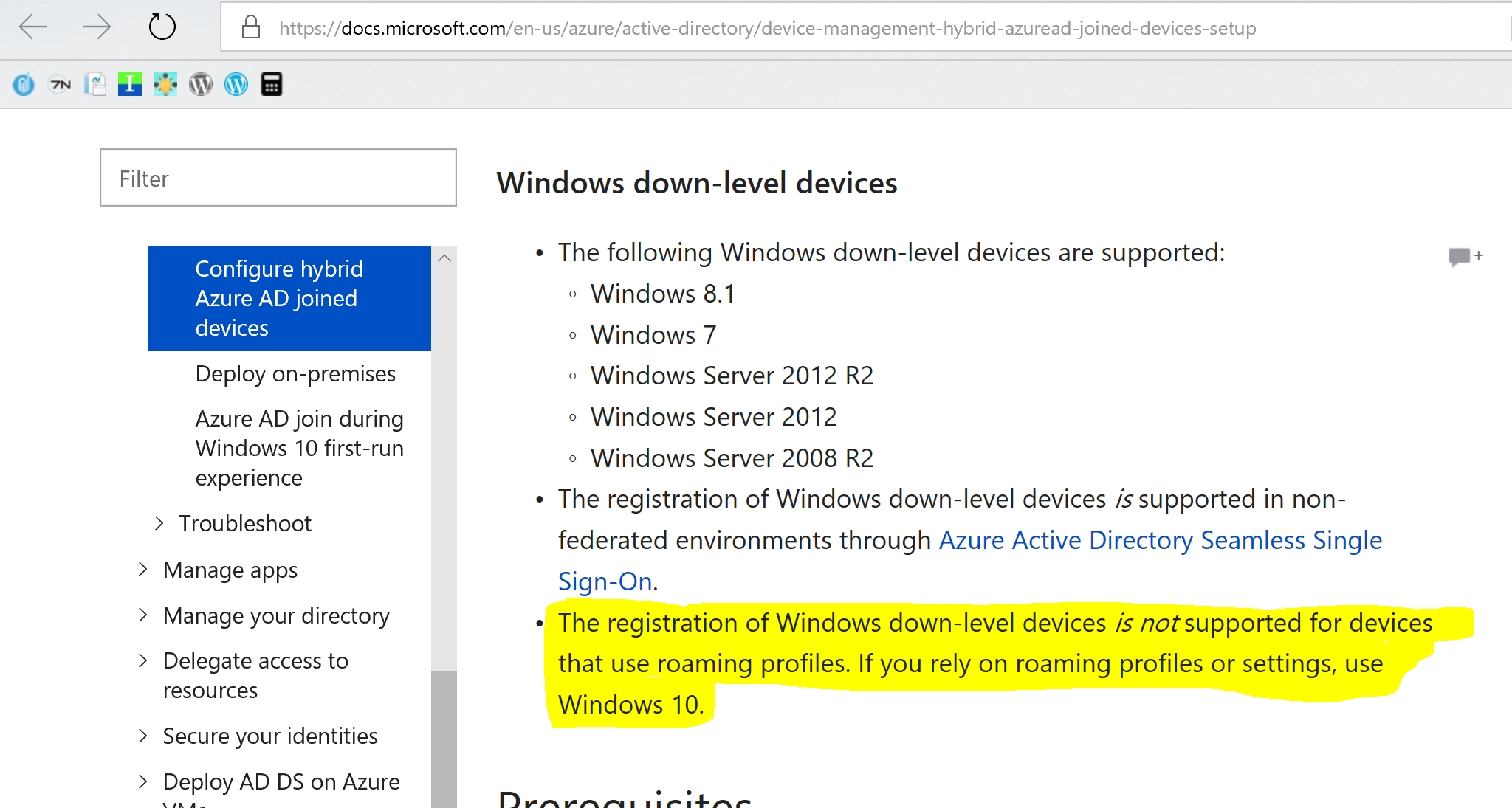
source: https://docs.microsoft.com/en-us/azure/active-directory/device-management-hybrid-azuread-joined-devices-setup
References:
- Public Key Authentication Protocol (PKeyAuth1.0)
- Troubleshooting Credential Roaming
- Microsoft Workplace Join for non-Windows 10 computers
- Credential Roaming
- Set up hybrid Azure Active Directory-joined devices
FAQ:
-
- Do you have any recommendation to when or how often to run this script? This would depend on the specific scenario, if you have decided to disable the use of credential roaming / roaming desktop you should only run the script once. Have you decided to keep using credential roaming / roaming desktop consider running the script during each login or at least once a week. It would depend on when and how often the users are getting prompted for selecting between the certificates.
/Peter